Reviews, reviews, reviews!

When we tell a Y Combinator batchmate that our company is “automating security and privacy reviews” the immediate answer we get back is “like SOC2?!” This makes sense - besides a fun Vanta billboard on the 101, SOC2 is often the first taste that startup founders get into the growing world of privacy, security, and compliance.
In this post, I’ll break down the types of reviews into three categories: (1) reviews of your company’s software; (2) reviews of your company’s overall posture; and (3) reviews of third party vendors (other company’s software) that integrate into your company or product.
Reviews of your company’s software
Security Reviews
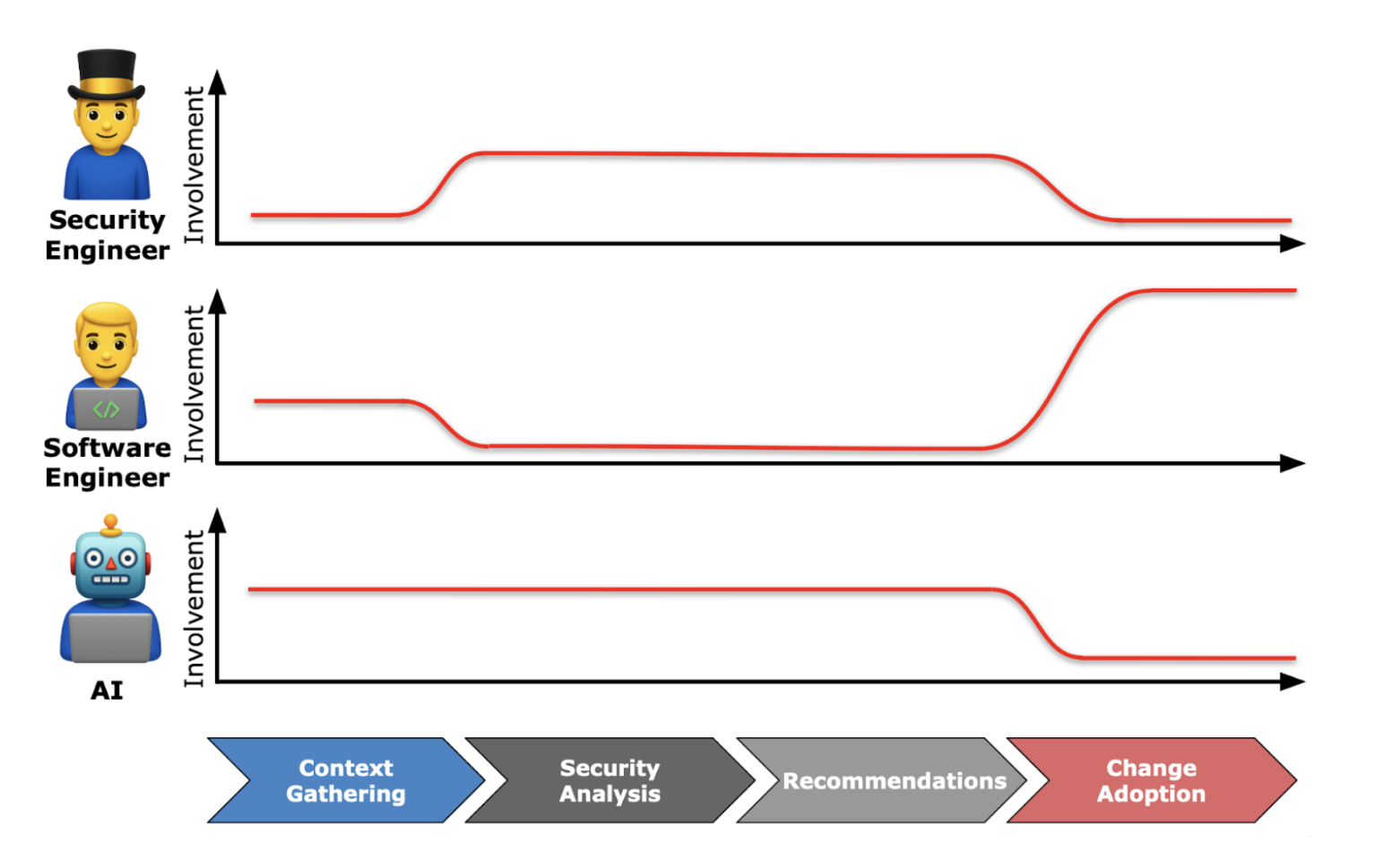
Security reviews, often called “product security reviews” or “application security reviews” focus on the security of the software you’re developing to sell to other customers or use internally as part of your business. Most product security reviews consist of a few components:
- Architecture review - understand the key components, infrastructure, and logic that makes up the product, and ensure it is secure by design. Architecture reviews typically include diagramming exercises like architecture diagrams and data flow diagrams.
- Threat modeling - the purpose of threat modeling is to think about the types of threats that could compromise the system and the controls in place to protect against them. It includes evaluating the network boundaries, assets, and actors. Folks often use a classic security framework like STRIDE.
- Code analysis - static code analysis tools (SAST), dynamic code analysis tools (DAST), and manual code reviews are used to ensure that the product was implemented as expected, and didn’t include vulnerabilities such as a lack of input validation or access control.
- Security testing - penetration testing, red teaming, and automated testing is sometimes incorporated for new products, risky products, or as part of CI/CD pipelines before deployment.
Privacy Reviews
Privacy teams also perform internal software reviews, such as “privacy by design reviews,” “privacy threshold analysis,” or “privacy impact assessments.” These reviews focus on privacy and compliance aspects like data handling, consent management, deletion, residency, and retention. Recently, many privacy teams have been tasked with AI Governance reviews as well. Privacy reviews normally include:
- Design requirements - many privacy risks are inherent to a feature’s design, such as the type of data collected or the combination of data together. Design reviews look at the bigger-picture goals of the new product and ensure privacy principles are followed.
- Data mapping - organizations need to map where all sensitive data is collected, processed, and stored. Data mapping exercises ensure that data is handled appropriately and allow the privacy team to evaluate each new data use case.
- Regulatory compliance - before launching a new product or feature, the privacy team must verify that compliance with applicable privacy regulations, such as GDPR or CCPA. These regulations each have nuances, but major product requirements include: supporting data subject access requests, data deletion, data retention requirements, and data residency requirements.
Reviews of your company’s overall posture
Overall company security, often called “corporate security” or “IT security” includes the security of your company’s infrastructure (office network, company laptops) and your company’s security policies (like password policies or incident response policies). Reviews of your corporate security may include product security reviews as well, though these are usually focused on network exposure and surface-level penetration testing.
Compliance (e.g., SOC2)
Audits to determine if your company achieves certain compliance frameworks, such as SOC2, are focused on your company’s overall corporate security posture. Compliance certifications ensure that basic security controls are enabled, including access control policies, change management policies, and audit logging.
For more information about compliance reviews, I’d recommend any of the many compliance vendors, like Vanta or Drata. Remember, while these vendors help automate compliance readiness, most certifications are granted by auditors, such as the AICPA for SOC2.
Security Questionnaires
Most enterprise security questionnaires or RFPs focus on the overall posture of your company, as their biggest fear is a supply-chain attack, where an attacker compromises their network, product, or data via their vendor. Security questionnaires normally include:
- Overall corporate security - enterprises will often ask for your internal security policies, any compliance reports you may have, and information about your incident response processes like timely breach notifications.
- Data handling and integrations - enterprises are very sensitive to the types of data you will handle as their vendor, and how you will integrate into their other systems. More sensitive data or integrations will require higher levels of due diligence.
- Available controls - enterprises often ask for higher security controls than smaller companies, including data segregation via single-tenancy, network segregation (private cloud or on-prem), and managed authentication (SSO).
- AI policies - increasingly, AI governance and usage have become a key component in security questionnaires. Enterprises are adverse to any AI companies training collective models using their data.
Reviews of your third party vendors
Just as enterprises must review you for security compliance, you are also responsible for reviewing your third party vendors. We recommend reviewing all vendors that will have access to your corporate network, will handle sensitive employee data, or will be a subprocessor (a handler of customer data). You can review vendors holistically for security, privacy, and compliance via a Vendor Risk Assessment.
Vendor Security Reviews
We recommend performing the same, or even a higher level of due diligence on your vendors as you would on any internal software you develop. Hold your vendors to as high a standard as possible, especially if they will handle personal, customer, or employee data. When performing a vendor security review, request access to the company’s trust center. Trust Centers should include an overview of the company’s architecture, key security controls, and any audits performed, including compliance certifications or penetration tests. Often with a vendor security review, you may not have sufficient visibility. We recommend asking deep and pointed follow-up questions to their team instead of sending a long vendor security questionnaire.
Vendor Privacy Reviews
If you provide any of your customer’s or employee’s data to a vendor as a subprocessor, you are responsible for that data. In GDPR, your company would be the “Data Controller” and subject to a higher level of scrutiny than a “Data Processor.” As the Data Controller, you have the overall responsibility to protect the personal data you receive. Performing vendor privacy reviews allows you to ensure your vendors comply with privacy regulations.
Feeling overwhelmed by all the reviews?
At Clearly AI, we believe all reviews should happen in one place, with the same tooling. Reach out to our team for help structuring your security and privacy review processes.

.png)

.png)